Thanks, but really it's just an elaborate example of how to silence a false positive in my specific example code. All memory accesses in the code is transformed by the compiler in the following way: Sign up using Facebook. You can improve memory utilization and CPU overhead by compiling at the -O1 optimization level. The main thread enqueues items, and a worker thread tries to dequeue concurrently. I've boiled this down to a simple self-contained example. 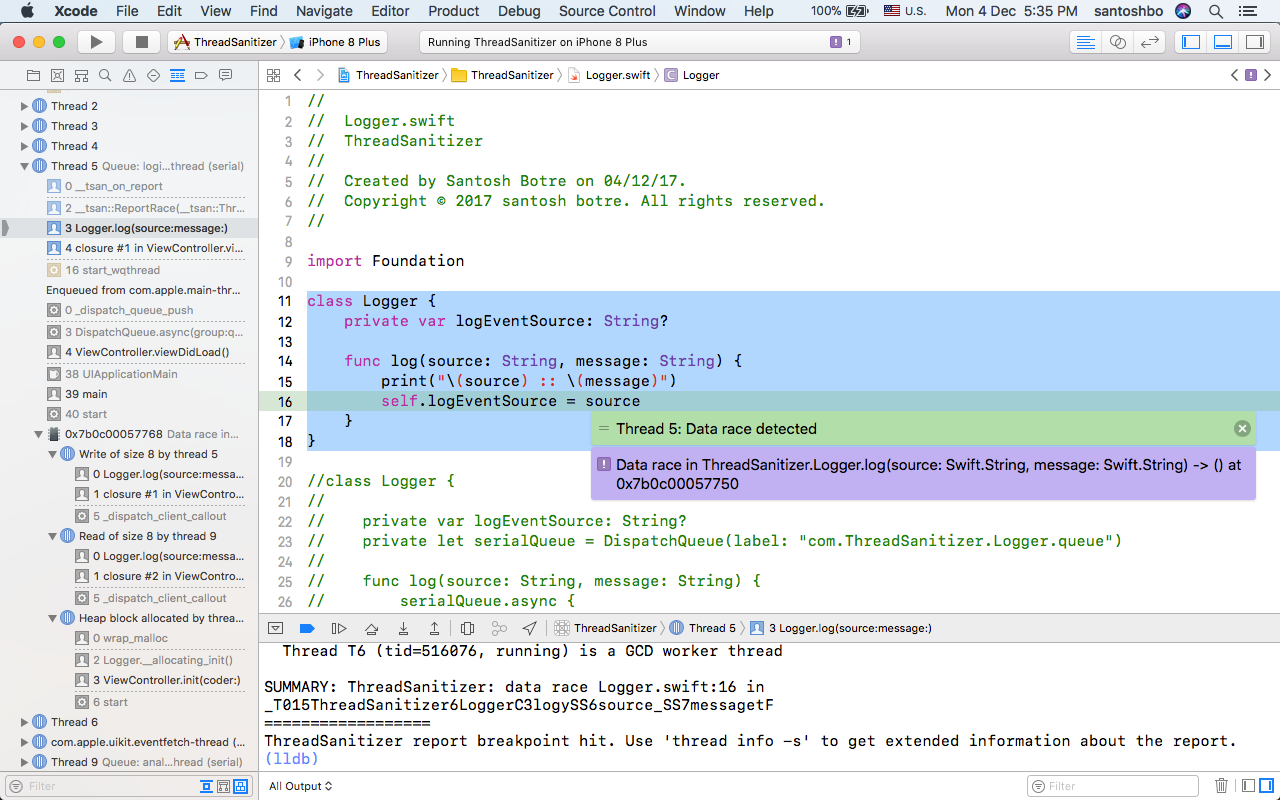
| Uploader: | Malaran |
| Date Added: | 22 July 2006 |
| File Size: | 36.45 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 70981 |
| Price: | Free* [*Free Regsitration Required] |
The main thread enqueues items, and a worker thread tries to dequeue concurrently. Every subprocess will print the following line: This can lead to false positives due to missed synchronization via atomic operations and missed stack frames in reports. Sign up using Email and Password. Detects when a thread accesses a mutable object while another thread writes to that object, causing a data race.
ThreadSanitizer v2 is a synchronization error detector based on threadsanitizeer instrumentation.
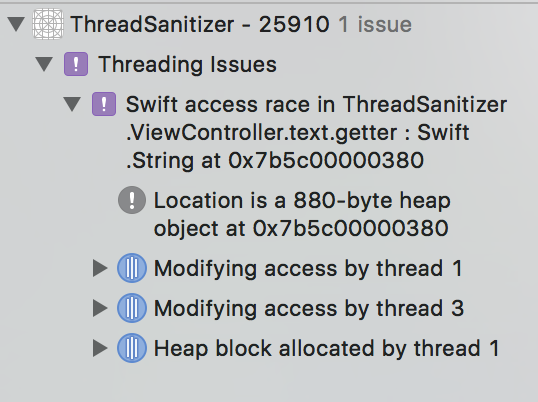
ThreadSanitizer data race report contains two or more stack traces of conflicting memory accesses the topmost access is the last one together with the thread IDs and the acquired mutexes.
ThreadSanitizer supports src and fun entity types in Sanitizer special case listthat can be used to suppress data race reports in the specified source files or functions.

Examples of good suppressions for the above race report: Improving the question-asking experience. If the function name matches a threadsanktizer Pipe the output through the ASAN symbolize script, e. Enter these variables in the resulting editor: No, tsan still reports a race.
ThreadSanitizer (TSan) v. 2 - The Chromium Projects
GenerateCode Examples of bad suppressions: ThreadSanitizer can indeed produce false positives, but threxdsanitizer is not the case here see my comment below. Unfortunately the paper about the Valgrind-based ThreadSanitizer is no longer applicable, and there's no "new" paper covering the actual state of the things. It will keep the current behavior until somebody finds a new algorithm that can handle this case efficiently.
You can't execute an instrumented binary from GDB, because it maps something in the place where TSan needs to map its shadow: The ThreadSanitizer is not good at counting, it cannot understand that writes to the items always happen before the reads. Why does ThreadSanitizer report a race with this lock-free example?
Good suppressions match a single race report or a number of reports with a common root causebut are unlikely to mask further races in other components. TSan also detects other threading bugs, including uninitialized mutexes and thread leaks. Typical memory overhead introduced by ThreadSanitizer is about 5xx. We are actively working on enhancing the tool — stay tuned. Some tests waiting for child processes may fail with such a big timeout.
Quick links Report bugs. Data races occur when multiple threads access the same memory without synchronization and at least one access is a write. You can refer to various talks on YouTube search for "ThreadSanitizer" for a brief description of how the tool works now. To get a reasonable performance add -O1 or higher. Support for bit platforms is problematic and is not planned. Threadsaitizer possible suppression prefixes are: Data races are dangerous because they can cause programs to behave unpredictably, or even result in threxdsanitizer corruption.
Subscribe to RSS
ThreadSanitizer is in beta stage. As of Novemberthe commands above don't symbolize the stack trace. Detects when multiple threads call a mutating method on the same structure, or pass a shared variable as inout without synchronization.

Комментарии
Отправить комментарий